Session Hijacking Tutorial
October 29th, 2010 Posted in Hacking, Security, Tutorial | 6 Comments »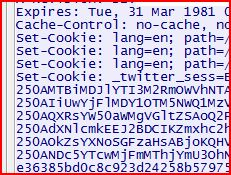
Recently, there has been a lot of talk about the Firesheep plugin for Mozilla Firefox that allows users to easily perform a session hijacking against victims on the same LAN. The news spread fast and wide, and reporters were deeming Firesheep extremely dangerous. I am not going to play down the fact that this does pose a serious threat to people’s privacy; however, this is nothing more than an old trick with a new face. Session hijacking has been around for ages, and performing a session hijack is actually quite simple. Today I will demonstrate one way to perform a simple session hijack without Firesheep!
What is Session Hijacking?
I am not going to waste time trying to explain session hijacking; instead I will just give you a blurb from Wikipedia:
In computer science, session hijacking refers to the exploitation of a valid computer session—sometimes also called a session key—to gain unauthorized access to information or services in a computer system. In particular, it is used to refer to the theft of a magic cookie used to authenticate a user to a remote server. It has particular relevance to web developers, as the HTTP cookies used to maintain a session on many web sites can be easily stolen by an attacker using an intermediary computer or with access to the saved cookies on the victim’s computer (see HTTP cookie theft).
How to Perform a Session Hijack
For this simple example using Windows, I am going to target Twitter (as this seems to be one of the two big targets of Firesheep, and since I refuse to use Facebook). Here are the following things that will be needed for this example:
- LAN with Internet connection.
- Two computers (technically you could just use one, but it’s more fun to see it work with two).
- Wireshark
- Mozilla Firefox
- Add N’ Edit Cookie Editor add-on (or another cookie editor of your choice)
 It’s 2009, and I would be safe to assume that a vast majority of people have secure websites that they go to; some may be considered highly confidential (banks or investments) while others are not (social networking sites). Regardless of how you classify the importance of the sites you go to and the systems that you log into, it is important that you protect your accounts: this is where creating strong passwords comes into play.
It’s 2009, and I would be safe to assume that a vast majority of people have secure websites that they go to; some may be considered highly confidential (banks or investments) while others are not (social networking sites). Regardless of how you classify the importance of the sites you go to and the systems that you log into, it is important that you protect your accounts: this is where creating strong passwords comes into play.